Write-ups for the SECCON 2019 capture the flag qualification round.
Unfortunately, I only got time to do a few (non-trivial) questions 😣 but problems were still interesting.
#Beeeeeeeeeer
Running this normally gives us:
Let's decording!(≧∀≦*)
which doesn’t do anything. So let’s take a look inside this challenge:
Instantly we can tell this is some place we shouldn’t be tampering but the first processing we can make to read this is:
- Evaluate the octal & hex escapes
- Break on newlines
- Indent
Here’s what that looks like:
What you are going to notice is a lot of:
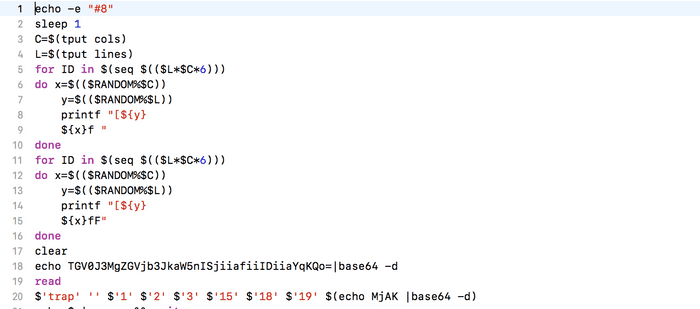
echo someCrap | rev | base64 -dand what this does is it’ll evaluate as bash the given base64 string. Sometimes it’s passed to gunzip but once we evaluate
Additionally you’ll see:
clear
echo "Let's decording!(≧∀≦*)"
read;
trapwhich is what was tricking us. We can remove this part from the script and then now we progress to the next part.
- The bell rings a few times, prompting you how many times it rand
- it asks for a password
We don’t need to RE more for the bell for but for the password we do. If we take a look at the next giant line we’ll see:
echo <massive block>
| base64 -D
| openssl aes-256-cbc -d -pass pass:$(
echo -n $n | md5sum | cut -c2,3,5,12
) -md md5 2>/dev/null
| bashand taking a look at this it just AES decrypts the base64 encoded block and executes that as bash. Here the key depends on $n our last which is set by the final bell which we can see rings 3 times. Once we decrypt this we have one final monster to conquer:
This is daunting but once you realize that:
- the
setcall is modifying traditional bash behavior $(. 2>&1)is actually'filename [arguments]'
So now we split the remaining monstrosity on ; and && and evaluate and one of the blocks is:
: password is bashand at the end you’ll see:
&&echo SECCON{$S1$n$_____}All of these variables were set before so we can now construct our flag SECCON{nandoku3bash}.